Can that include real news on it? Right now there is like one thing that has been said by p0sixninja about it. I'd like to get updates, unless its from some crap blog that uses that same tweet to say it is almost done. I'd imagine we're pretty far away from an actual jailbreak.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
IPAD 2 jailbreak 4.3
- Thread starter Argyle
- Start date
- Status
- Not open for further replies.
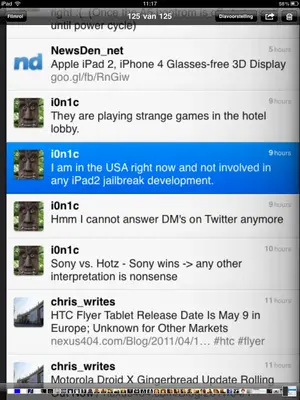
Well, some news; i0n1c is not working on a iPad 2 JB right now. xD
Sent from my iPad 2 using iPF
We all deserve a break now and again right?
SweetPoison
iPF Noob
Well, some news; i0n1c is not working on a iPad 2 JB right now. xD
Sent from my iPad 2 using iPF
We all deserve a break now and again right?
umm....you never take one, Leigh!
Can someone tell what this means?
Sent from my iPad 2 using iPF
My view would be as follows:
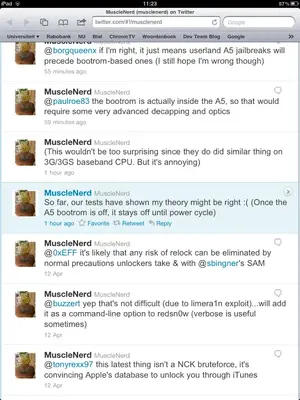
The bootrom is a read-only portion of the processor where the device starts up. What we really want to find is an exploit in the new iPad2 A5 bootrom code, just like the ones we have for previous devices, including iPad1 and iPhone4. The thing about a known bootrom exploit is, once we have it, Apple cannot fix it without changing the hardware.
What MuscleNerd is saying is that once the bootrom on the iPad2 has finished its stuff (which is early in the bootup process) it is switched off at a hardware level (powered down) and does not get reactivated at any time until the next time the device boots. This will make it quite a challenge for anyone to actually see what is going on in the bootrom by dumping it. Some of the twitter responses are suggesting that a hardware dumping solution would need to be found. i.e. take the iPad2 apart and start soldering! Needless to say that would be a real drag...
Hence, his latest update which states we are likely to see a userland jailbreak first, rather than a bootrom based one...
Last edited:
RudyL90
iPF Noob
f4780y said:We all deserve a break now and again right?
NO!
Well of course.
Sent from my iPad 2 using iPF
RudyL90
iPF Noob
f4780y said:My view would be as follows:
The bootrom is a read-only portion of the processor where the device starts up. What we really want to find is an exploit in the new iPad2 A5 bootrom code, just like the ones we have for previous devices, including iPad1 and iPhone4. The thing about a known bootrom exploit is, once we have it, Apple cannot fix it without changing the hardware.
What MuscleNerd is saying is that once the bootrom on the iPad2 has finished its stuff (which is early in the bootup process) it is switched off at a hardware level (powered down) and does not get reactivated at any time until the next time the device boots. This will make it quite a challenge for anyone to actually see what is going in the bootrom by dumping it. Some of the twitter responses are suggesting that a hardware dumping solution would need to be found. i.e. take the iPad2 apart and start soldering! Needless to say that would be a real drag...
Hence, his latest update which states we are likely to see a userland jailbreak first, rather than a bootrom based one...
I am not sure I understand now, but thanks for the explanation!
Sent from my iPad 2 using iPF
Last edited:
iRager
iPF Novice
f4780y said:Hence, his latest update which states we are likely to see a userland jailbreak first, rather than a bootrom based one...
Comex's 4.3 jb is userland so we most likely will be seeing that first right?
Serianni
iPF Noob
ZibaWal said:Can u please advise me how to do so?
Well if you still have not updated it and still have 4.3 then just get tiny umbrella
Comex's 4.3 jb is userland so we most likely will be seeing that first right?
It is certainly more likely based on the (limited) information we all have. The problem, as I understand it, with the 4.3 userland JB which Comex has is it relies on Apple licensed code which therefore cannot be distributed without resulting is swift and undoubtedly heavy handed legal proceedings from Apple.
So, to get it in a releasable state, a freely licensed alternative needs to be found / developed. That has the potential to be just as complex as getting in about the bootrom. But the truth is, I don't know the detail, and neither do many other folks. It's just speculation.
I am sure a solution will be found. These guys are at the top of their game. It's fun to speculate, but ultimately they could easily make us all look like fools by coming up with a new usable exploit tomorrow... Here's hoping.
+1 for ipad 2 jb tomorrow
+10 for ipad 2 jb today!!!
I'm new to forums, but you guys are awesome. I have been searching for answers all over the place. Got an IPAD2 64GB about 3 weeks ago but also have a JB iphone. cant really do squat with the ipad compared to what i can with the phone. Cant wait for this dam JB so i can actually start using this thing
- Status
- Not open for further replies.